|
The Interview: Hacking American Culture
Daniel Drew,� 12/20/2014 From George Washington to Steve Jobs, hacking is part of American history. 
The Interview's downfall is actually the most successful marketing campaign in all of history. Create a movie about assassinating a deranged narcissistic dictator, market the absurdity of that movie, attract the attention of the dictator, incur the wrath of his computer nerd army, have the President endorse the viewing of your movie as a patriotic duty, and then pull it at the last minute because some computer geeks said they would blow up theaters. What started as a standard fringe comedy turned into the fixation of the entire country. Sony, you have our attention. The latest Sony situation shouldn't be that surprising if you recall the PlayStation hack of 2011. In a letter to the U.S. House of Representatives, Kazuo Hirai, the Sony Chairman, said the personal information of 77 million people had been hacked. 2.2 million credit card numbers were stolen. Moreover, it took them a full week before they decided to tell anyone about it. The PlayStation Network was eventually offline for 23 days. You would think Sony might have learned from that embarrassment. It's amazing people still have trust in the brand. Sony reminds me of hedge fund managers who blow up over and over, and they just start new funds anyway. Early Warning The North Koreans complained about The Interview in July. Ja Song Nam, the North Korean ambassador, wrote a letter to UN Secretary-General Ban Ki-moon: "The United States authorities should take immediate and appropriate actions to ban the production and distribution of the aforementioned film; otherwise, it will be fully responsible for encouraging and sponsoring terrorism." They have a point. If the jihadis released a movie about an Arab leader going to visit Obama at the White House, only to betray the President's trust and launch an assassination attempt, the American media would quickly label it as a propaganda movie. Americans would look down at the "crazy Muslims" and despise them for their barbarism. There would be no discussion about the jihadis' First Amendment rights. You can make a satirical movie about killing Kim Jong-un, but if you make a movie about killing Obama, you better believe there will be eyes on you for the rest of your life. The hackers claim to have stolen 100 terabytes of internal Sony files and films. If you're a normal person, you don't know what that means. Here is a chart to help you understand how much data we're talking about. Here's another way to think about it: If the data were nothing but movie files, it would be 50,000 hours of movies. 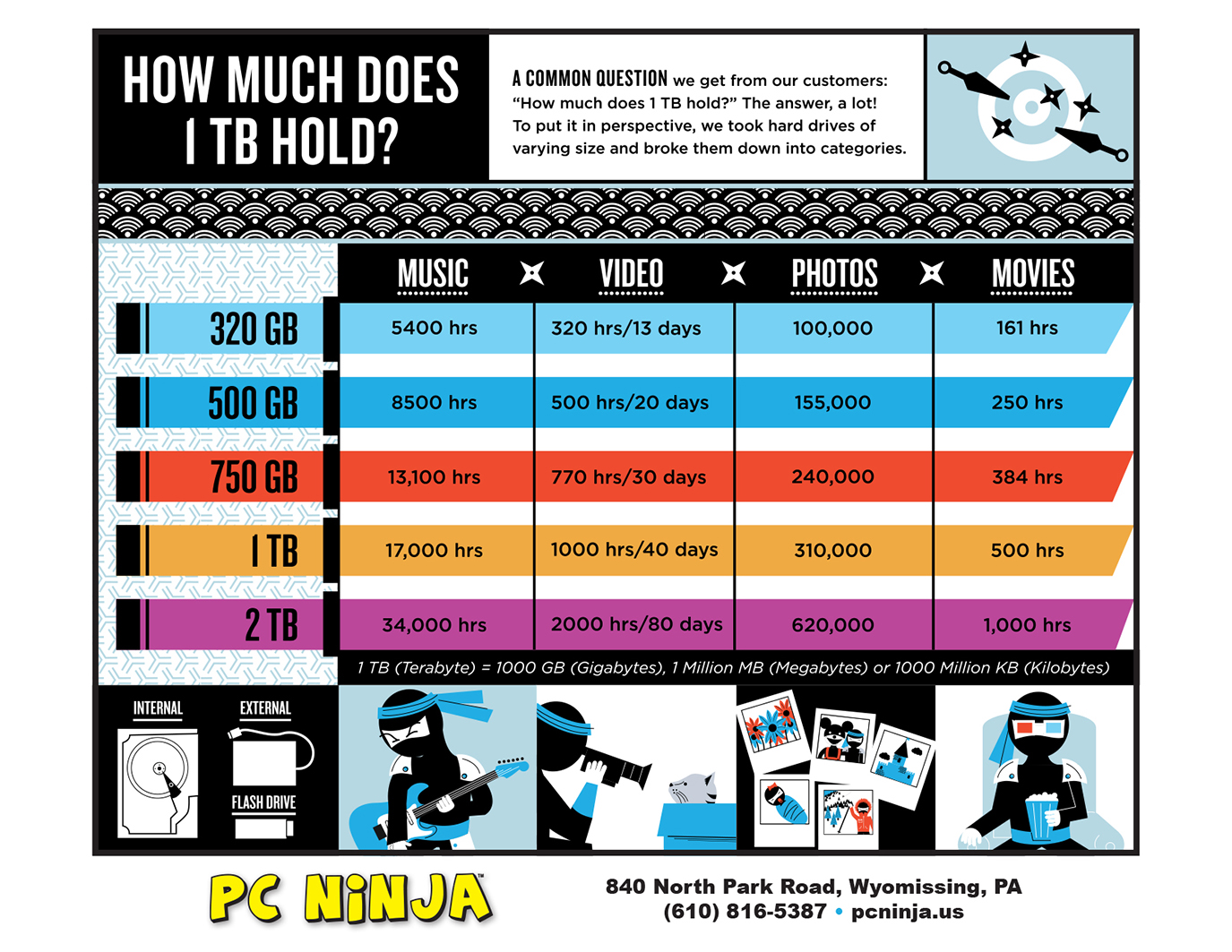
Some amusing gems were released in the huge data drop, including billionaire Mark Cuban's outrage over receiving only $30,000 per episode for his appearances in season 5 of Shark Tank. Oh the humanity! The billionaire only gets $30,000 for his TV show. I'll be sure to remember to include Mark on my Christmas card list this year. "Dear Mark: Tis the season to be jolly - unless it's season 5." Sony is fighting back with its own denial of service attacks using hundreds of computers in Asia. It is targeting sites that are hosting the pirated movies. Unclear Origins Furthermore, it's not even clear if North Korea was behind the hack. Probable cause definitely exists, but that's just not enough. We need evidence, and with hacking cases, that evidence is often extremely elusive. Tech magazine "Wired" said, "attribution is difficult if not impossible." Pro hackers use proxy computers and fake IP addresses to carry out their attacks. In non-technical jargon, what this means is that if you're sending a bomb threat to the White House, you're definitely not going to put your home address sticker on the envelope. Even worse, the hackers create false clues - and not just a single one, like one fake address on an envelope. I have heard all kinds of theories about who did it: a disgruntled Sony insider seeking revenge, the Chinese, a hacker activist group, and everybody. Even if the FBI says it was so and so, you can't believe them. The only people who have the best chance of uncovering the source are the ultra hackers at the National Security Agency (NSA) because they are not constrained by the legal system. The North Koreans have repeatedly denied any involvement, even going as far as proposing a joint investigation into the incident. They took a shot at the CIA in their statement, "Without resorting to such tortures as were used by the CIA, we have means to prove that this incident has nothing to do with us." They may have been referring to an August statement by Obama, when he said, "We tortured some folks." The Essence of a Hack You can get a dozen technologically sophisticated people together, and each of them will give you a different explanation - much more complicated than you wished for. A hack is nothing but an ambush. Someone poured water on your head when you opened the door? You got hacked. The only variations of a hack are in the levels of technological involvement. But one must always start with the most basic concept of a hack. I can think of no simpler image than a bucket of water on your head. The First Hack If you want to complicate the definition of hack and say it must require some more advanced technology, fine. In that case, you could say the first hack was done by Nevil Maskelyne, a 39-year-old British music hall magician. In June 1903, the physicist John Ambrose Fleming was giving a presentation at the Royal Institution's lecture theater in London. He was demonstrating a new technology by the Italian radio pioneer Guglielmo Marconi: a wireless telegraph machine that could send Morse code messages over 300 miles. Just as Fleming was about to begin his presentation, he got hacked. The machine was tapping out a message: "There was a young fellow of Italy, who diddled the public quite prettily." Just imagine Steve Jobs as he announced the iPhone for the first time. What if he got a text message that displayed on the projector that said, "There was a man in Silicon Valley, who bungled his phone like a man from the jungle." This is the kind of extraordinary embarrassment that took place. As Maskelyne demonstrated, the internet is not required for hacking. He justified his behavior with the same excuses "good hackers" use today: to identify risks to the public. The only harm that occurred was to Fleming's ego. Hacking in World War II Hacking continued to play a critical role in history, with Alan Turing and his fellow codebreakers in Britain hacking the German cipher machine that Hitler used to communicate with the Nazis. The British government was so wary that they did not disclose the details of these efforts until 1974, 29 years after the war ended. Some historians think the hacking of German war communication shorted the war by two to four years, saving millions of lives and altering the course of history. Steve Jobs and Steve Wozniak: American Hacker Heroes In the 1970s, "phone phreaking" became a phenomenon. By sending specific audio tones, you could control long distance trunk lines and make international calls for free. Steve Wozniak designed a digital blue box to generate the necessary tones, and Steve Jobs decided they could make money selling it. In an interview with the Silicon Valley Historical Association, Jobs said that if it hadn't been for their illegal blue box sales, there would have been no Apple. So there you have it. The founders of the largest company in the world were inspired by hacking. Steve Jobs called it "magic." They became American hacker heroes. Viruses and Hacker Groups Proliferate In June 1994, a Russian hacker used his computer in his apartment in St. Petersburg to access a Citibank computer in New York. His reward? $10 million of stolen money. As the internet proliferated, it became much easier to hack massive amounts of people. It seemed like every year there was a new virus making its way around the world. Some of the worst were the I love you email attachment virus in 2000, Code Red (2002), Slammer (2003), Fizzer (2003), MyDoom (2004), Poison Ivy (2005), Zeus (2007), agent.btz (2008), Conficker (2009), and Stuxnet (2009). Agent.btz was found on computers at the Pentagon, and the military had to create an entire new unit to deal with it: U.S. Cyber command. Hacking groups also formed. Instead of breaking legs and kneecaps like the mafias of yesteryear, they broke firewalls and passwords - probably while drinking soda and eating chips in their underwear. Anonymous, one of the most famous hacking groups, captured the spotlight in 2008 when they launched Project Chanology, an effort to undermine the Church of Scientology. Anonymous even made the list of Time Magazine's 100 most influential people in 2012, despite the fact that they were a shadow group and not a single person. In June 2011, Lulz Security launched successful denial of service (DOS) attacks on the websites of the CIA, PBS, Sony, and the U.S. Senate. Even Bitcoin, the alleged currency of the future, was not immune to the effects of hackers. In March, Mt. Gox, the largest bitcoin exchange in the world, declared bankruptcy after losing $460 million of bitcoins, supposedly taken by hackers. All of this merely reinforces the critics of all things digital. The electronic world appears more ephemeral than ever. Perhaps one day we will shun technology and revert to objects that we can hold in our hands - and I'm not talking about iPhones. Operation Olympic Games Just like Watergate, sometimes the hacking goes all the way to the top. Almost as soon as Obama took office in 2009, he took charge of Operation Olympic Games, a joint American-Israeli project that began in the Bush Administration. The goal: hack Iran's nuclear centrifuges at the Natanz nuclear facility and take them offline. Their efforts eventually caused 20% of Iranian centrifuges to spin out of control. The virus became known as the Stuxnet virus. It was delivered via a worker's USB flash drive. In summer 2010, a coding error caused the virus to replicate across the world. One day, this is probably how Skynet will become self-aware. Everyone thinks they can contain the beast. They can't. In typical vice president fashion, Biden dodged blame: "It�s got to be the Israelis. They went too far.� It was never determined who made the programming error. A week later, Stuxnet wiped out 1,000 Iranian centrifuges. So one day if you turn on CNN and see a huge nuclear explosion in Iran, you'll know what happened. According to participants in Situation Room meetings about Olympic Games, Obama obsessed over the implications of his brazen cyber warfare: any official American acknowledgement of its activities could enable other countries, terrorists, or hacker groups to justify their own attacks using the same logic. Do as I say - not as I hack. Hacking's Effect on Business The hack at Sony was absolutely crippling. Aside from the easily recognizable losses like illegal movie downloads, the loss to its brand is enormous. It could be much worse than the PlayStation hacks. Millionaire actors and actresses might not be as forgiving about privacy violations as 15-year-old video gamers. Come be in the next Sony blockbuster, and get hacked! There is also the issue of the behind the scenes gossiping by Sony bosses about how the celebrities are such jerks. If I were an A-list movie star, I would never work with Sony again. I have options. I don't need them. They need me. If the worst case scenario were to play out, it would be a significant blow to Sony, but not necessarily devastating. The Japanese multinational has about $75 billion in annual revenue. Sony Pictures only brings in $8 billion of that. More important to Sony are the sales of its PlayStation console and smartphones. Sony as a company is doing well - allegedly. Sales were up 14% in 2014. However, on a constant currency basis, sales decreased 2%. This means the company is stagnating and is only gaining nominal sales from the weak yen. But even if companies take hacking related losses, the real loser is the consumer - or in the case of the Sony hack, the employee. An anonymous Sony Pictures employee said, "It�s taken a toll, mentally - do I have to worry about someone getting a random medical procedure with my benefits? You always have to look over your shoulder. This is forever." Meanwhile, Sony stock hasn't taken any hits since the hack occurred. No losses for the shareholders. Hacking: The American Way In the aftermath of the hack, George Clooney circulated a petition in Hollywood to support Sony's decision to try to release the film in some way. He said he wanted to support the First Amendment. Some are even calling the hack the end of free speech in Hollywood. But is that what this is really about? Did the Sony hackers actually stop Sony from releasing The Interview? If you look closely at history, what you'll find is the relentless persistence of the basic human desire to speak one's mind. Even in countries without First Amendment protections, people find a way to speak. They always have, and they always will. The First Amendment exists just to make that process a little easier. The Sony hackers made it a little harder, but Sony Pictures and the theaters still have freedom of speech and the freedom to choose between cowardice and courage. This isn't about freedom of speech. It's about hacking. Is hacking Un-American? If it is, then Kim Jong-un is attacking American culture. But what have we learned from American history? George Washington is the ultimate American. He was the Commander-in-Chief of the Continental Army during the American Revolutionary War and the first American president. He was also the first American hacker. Washington maintained elaborate spy rings to gather essential information about the enemy. He also sent out false signals to confuse the British, much like the false signals the Sony hackers are leaving to confuse the FBI. The spies even used invisible ink. In modern technology parlance, this is called "encryption." In his ultimate hack, Washington crossed the Delaware River on Christmas Day in 1776 to ambush the Hessian mercenaries. The Continental Army crossed the river in the middle of the night during a severe winter storm. It was a bold move, and they defeated the Hessians at the Battle of Trenton. The Hacker-in-Chief prevailed. From the founder of the nation to the scheming industrialists of the 1800s to the Apple founders to the President hacking Iranian nuclear centrifuges, it becomes clear that hacking couldn't be any more American. Hacking is an ambush designed to exploit the weakness of your opponents. Our capitalist system promotes it, requires it, and demands it. We have laws to limit the ways we ambush each other, but within those laws, the hacking ideal remains. Kim Jong-un didn't hack American culture. While he violated the law, the spirit of his actions were at the core of the American character. |